How to Check Phishing Emails Fast
Phishing emails have become one of the most common and dangerous digital threats. These deceptive messages try to trick you into clicking on malicious links or downloading harmful attachments.
Falling for one can mean handing over personal information or allowing malware into your system, which can have serious consequences. But don’t worry—checking suspicious emails doesn’t have to be complicated.
Here’s how you can quickly identify potential threats and keep your information safe.
Common Signs of a Phishing Email
Phishing emails often disguise themselves as messages from trusted sources, like banks, colleagues, or popular online services. They aim to create a sense of urgency, making you feel like you need to act fast.
It’s important to be cautious before clicking any links or opening attachments, as these could be gateways for malware.
Spotting a phishing email can be easy if you know what to look for. Below you can find common red flags:
- Unusual email address: Even if the sender’s name looks familiar, double-check the email address. A slight misspelling or random characters can signal a fake email.
- Poor grammar and spelling mistakes: Legitimate businesses typically proofread their emails, so multiple errors can be a warning sign.
- Unexpected attachments or links: Be wary of attachments or links that you weren’t expecting, especially if the email insists you open them right away.
- Urgent language: Words like “immediately,” “urgent,” or “action required” can be signs that the sender is trying to manipulate you into clicking without thinking.
The Easiest Way to Check Suspicious Emails
If you receive an email that raises any of the red flags, don’t panic. You can quickly verify its safety by using a sandbox tool like ANY.RUN.
A sandbox is a secure, virtual environment where you can safely analyze emails and attachments without risking your computer’s security.
| Sign up for ANY.RUN’s sandbox for free and perform unlimited analyses |
Here’s how to do it:
Upload or paste the email
Take the suspicious email or its link and upload it into the sandbox. This way, you can examine it without the risk of running any harmful code on your computer.
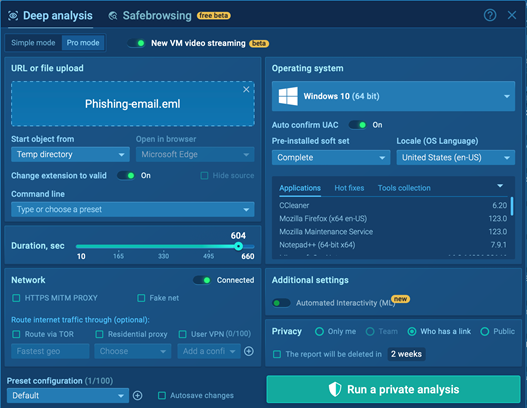
Uploading suspicious email inside ANY.RUN’s sandbox
Analyze the email in a virtual machine
The sandbox lets you open the email in a virtual environment, where you can observe how it behaves.
In the following session analyzed inside ANY.RUN’s sandbox, the email claims that a payment was made incorrectly and asks the recipient to review the attached document to correct the amount.
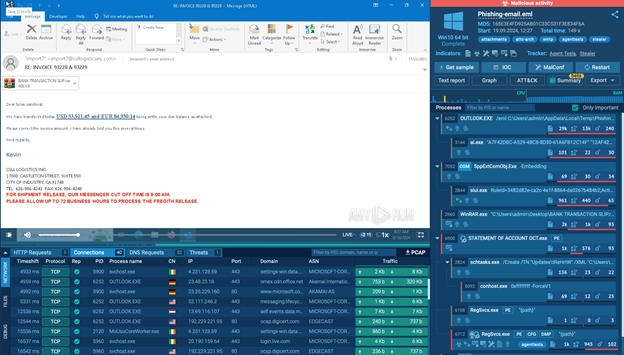
Suspicious email displayed inside ANY.RUN’s sandbox
The attachment is labeled “STATEMENT OF ACCOUNT,” but once opened in the sandbox, it’s clear that it contains a hidden executable file—a type of file that is unusual in everyday business emails.
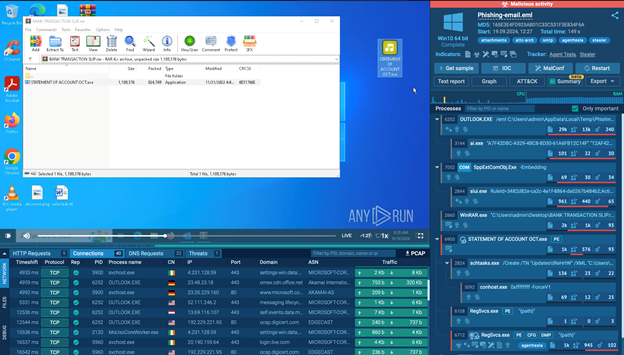
The downloadable archive analyzed inside sandbox
By opening the attachment inside the sandbox, you can see exactly what happens when the file is run. As the analysis progresses, the sandbox detects that the file is actually a type of malware called Agent Tesla.
This particular malware can steal sensitive information and monitor your activities without you knowing.
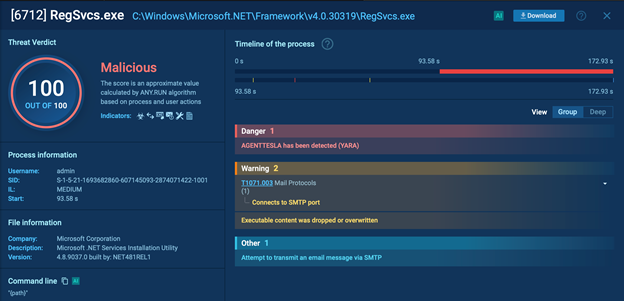
Agent Tesla detected inside ANY.RUN’s sandbox
How to Quickly Identify Malware in the Sandbox
- Look for the warning label: After the sandbox finishes analyzing the email, a warning label appears in the upper right corner. If it’s red and reads “Malicious Activity,” it’s a clear sign that the email isn’t safe to open on your computer.
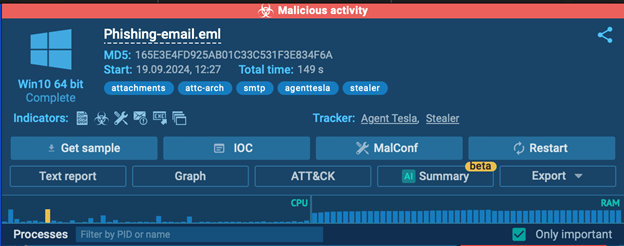
Malicious activity detected by ANY.RUN’s sandbox
- Check the process tree: For a more in-depth look, you can explore the process tree. This will show you each action the malware takes, providing valuable insight into how the threat operates.
Click on individual processes to learn more about the attack’s behavior.
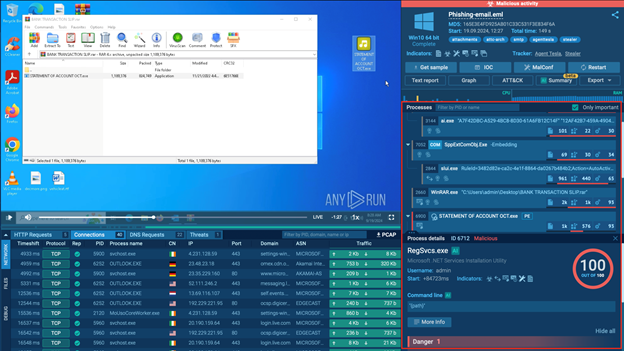
Process tree inside sandbox
Analyze Suspicious Emails Faster Inside a Safe Environment
By using an interactive sandbox such as ANY.RUN, you can quickly and safely analyze suspicious emails before they reach your inbox. This tool allows you to inspect attachments and links without any risk to your device, giving you peace of mind.
And if you’re unsure about an email’s authenticity, running it in the sandbox can provide a clear answer.






